E-pismo dla elektryków i elektroników
AUTOMATYKA, ELEKTRYKA, ZAKŁÓCENIA
Vol. 7, Nr 4(26) 2016
Malware – złośliwe oprogramowanie w systemach IT/OT
Malware - malicious software in IT/OT systems
dr inż. Tomasz GIERSZEWSKI
Abstract
The article presents a survey on IT/OT security threats related to malicious software. The review relates to the threats along with their evolution over time as well as means to mitigate them. Not only theoretic approach has been presented, but solutions available on the market and best practices as well. The paper also considers the security of IT/OT systems interconnection.
Streszczenie
W artykule zaprezentowano przegląd zagrożeń bezpieczeństwa IT/OT związanego ze złośliwym oprogramowaniem. Scharakteryzowano zarówno zagrożenia, w szczególności ich ewolucję, jak i sposoby ich zwalczania. Zaprezentowano nie tylko teoretyczne ujęcie zagadnienia, ale także rozwiązania dostępne na rynku i dobre praktyki. Odniesiono się również do zabezpieczania styku systemów IT/OT.
Keywords
security, malware, IT/OT
Słowa kluczowe
bezpieczeństwo, malware, IT/OT
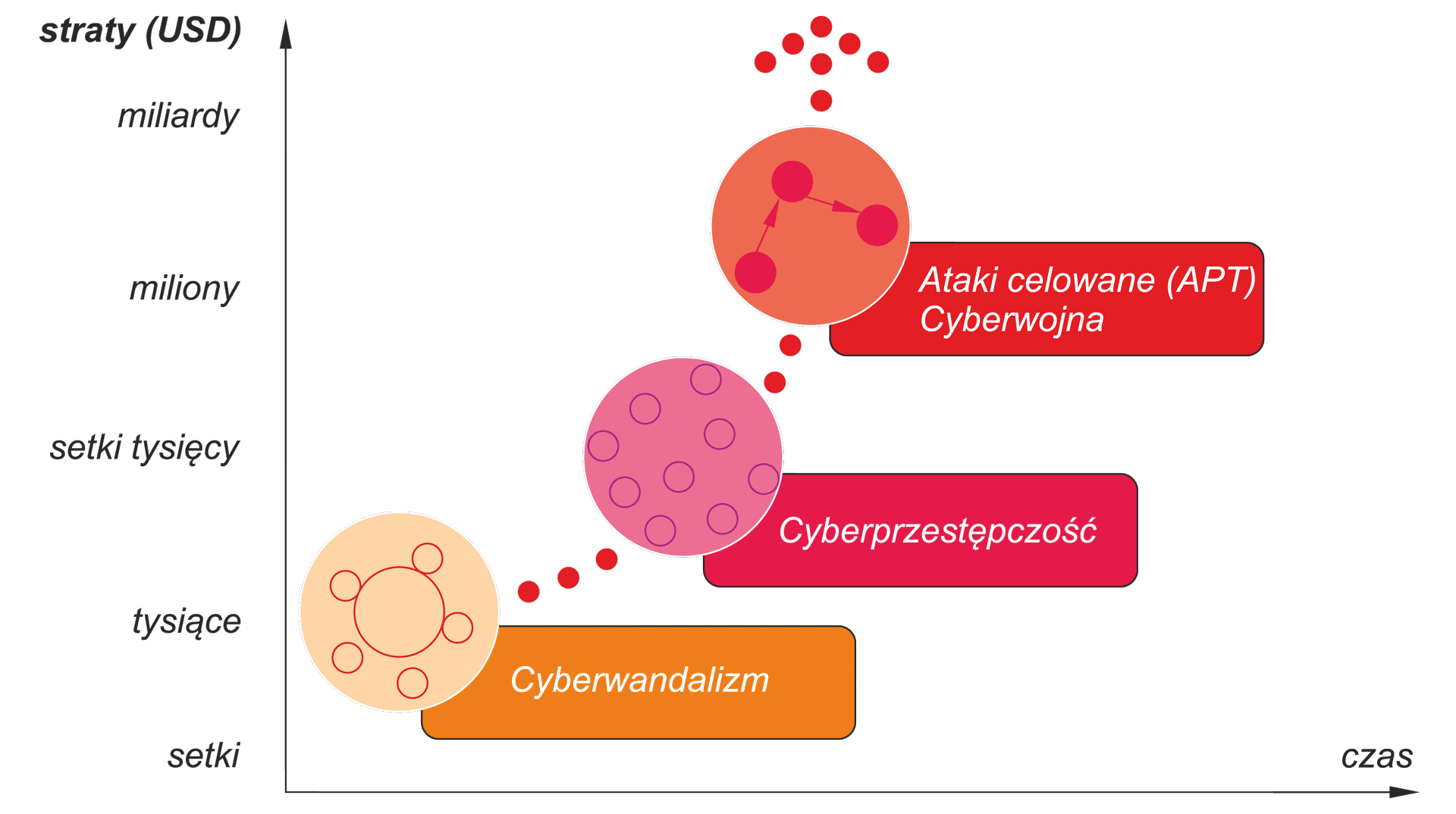
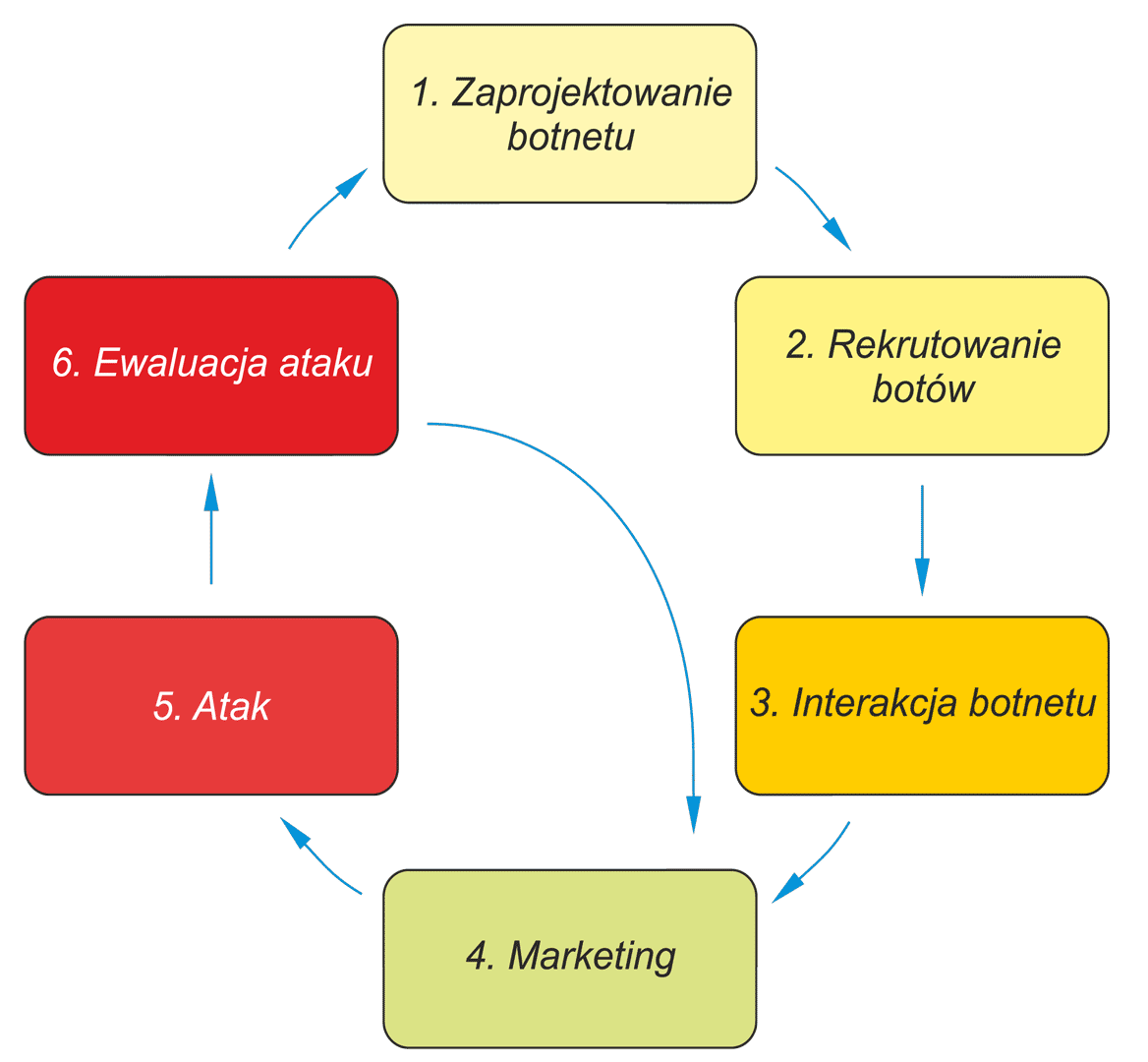
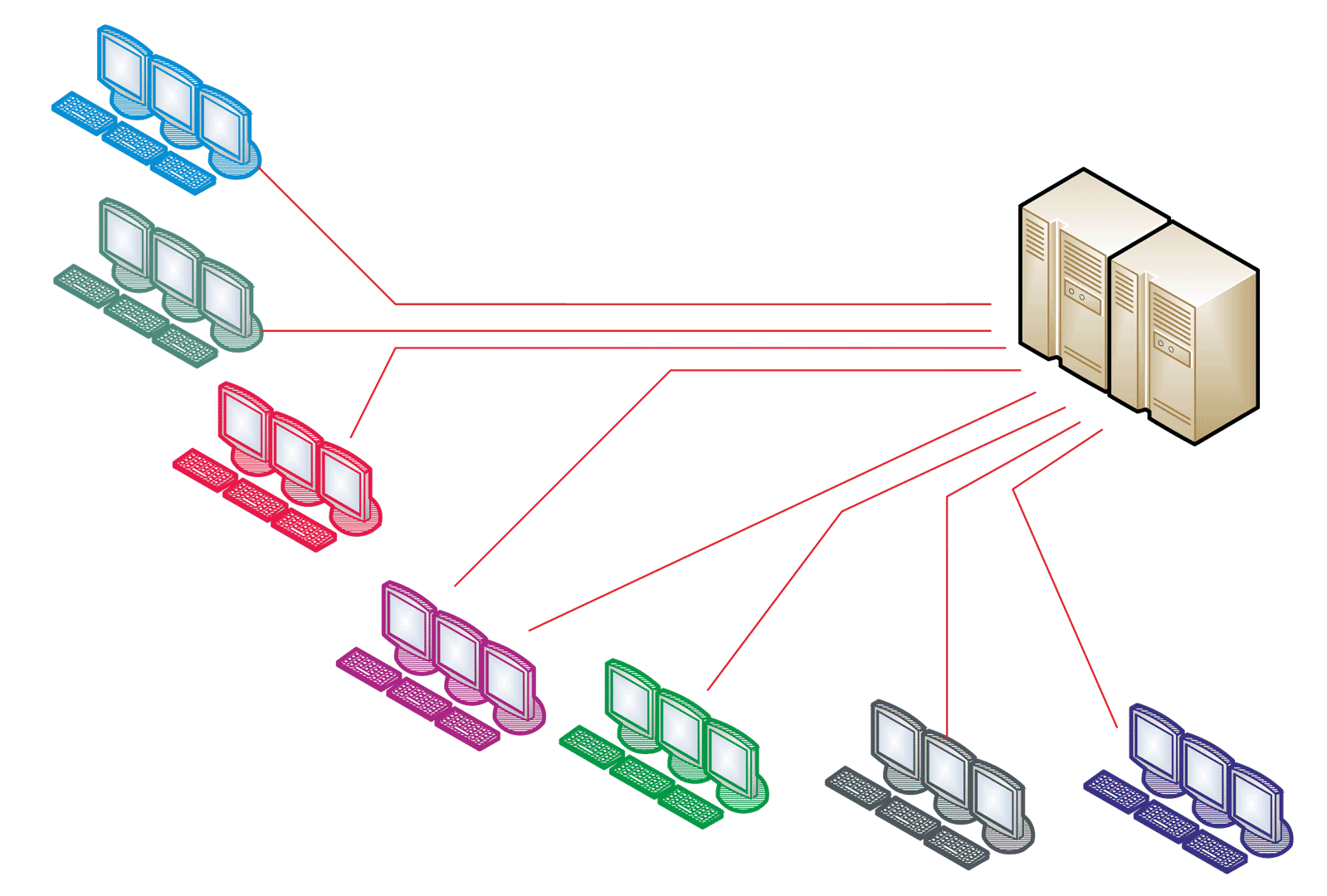
Rys. / Fig.
Bibliografia / Bilbiography
[1] E.W. Burger, M.D. Goodman, P. Kampanakis, K.A. Zhu, “Taxonomy Model for Cyber Threat Intelligence Information Exchange Technologies.”, In Proceedings of the 2014 ACM Workshop on Information Sharing & Collaborative Security, ACM, 51-60, 2014
[2] P. Čeleda, J. Vykopal, T. Plesník, M. Trunečka, V. Krmíček, “Malware detection from the network perspective using netflow data”, In 3rd NMRG workshop on NetFlow/IPFIX usage in network management, 2010
[3] W. Chang, A. Mohaisen, A. Wang, S. Chen, “Measuring botnets in the wild: Some new trends”, Proc. of the 10th ACM SICCS, 645-650, 2015
[4] Cyber-Attack Against Ukrainian Critical Infrastructure, ICS-CERT IR-ALERT-H-16-056-01, https://ics-cert.us-cert.gov/alerts/IR-ALERT-H-16-056-01, 02.2016, dostęp 01.2017
[5] Cyber-Attack Against Ukrainian Critical Infrastructure-Update A, ICS-CERT IR-ALERT-H-16-056-01-AP, http://www.eenews.net/assets/2016/07/19/document_ew_02.pdf, 03.2016, dostęp 01.2017
[6] K. Dunham, “Mobile malware attacks and defense”, Syngress.
[7] N. Falliere, L.O. Murchu, E. Chien,i in., “W32. stuxnet dossier”, White paper, Symantec Corp., Security Response, 5, 2011
[8] J. Franklin, A. Perrig, V. Paxson, S. Savage, “An inquiry into the nature and causes of the wealth of internet miscreants”, ACM conference on Computer and communications security, 375-388, 2007
[9] T. Gierszewski, W. Molisz, „Ataki DDoS – przegląd zagrożeń i środków zaradczych”, Przegląd Telekomunikacyjny + Wiad. Telekom., 8-9, 720-728, 2014
[10] R. Goyal, S. Sharma, S. Bevinakoppa, P. Watters, “Obfuscation of stuxnet and flame malware”, Latest Trends in Applied Informatics and Computing, 2012
[11] K.W. Hamlen, V. Mohan, M.M. Masud, L. Khan, B. Thuraisingham, “Exploiting an antivirus interface”, Comp. Standards & Interfaces, 31(6), 1182-1189, 2009
[12] R. Khan, P. Maynard, K. McLaughlin, D. Laverty, S. Sezer, “Threat Analysis of BlackEnergy Malware for Synchrophasor based Real-time Control and Monitoring in Smart Grid”, 4th International Symposium for ICS & SCADA Cyber Security Research, 53–63, 2016
[13] M. Ligh, S. Adair, B. Hartstein, M. Richard, “Malware analyst's cookbook and DVD: tools and techniques for fighting malicious code”, Wiley Publishing, 2010
[14] J.A. Marpaung, M. Sain, H.J. Lee, “Survey on malware evasion techniques: state of the art and challenges”, 14th Int. Conference on IEEE Advanced Communication Technology (ICACT), 744-749, 2012
[15] R. McArdle, “How much is your life worth?”, 16th Secure Conference, Warsaw, 2012, dost. 02-2015: http://www.secure.edu.pl/pdf/2012/D2_1745_P_McArdle.pdf
[16] D. Mcwhorter, “APT1: Exposing One of China’s Cyber Espionage Units”, Mandiant. com, 18, 2013
[17] R. Piggin, “Critical Infrastructure Under Attack”, ITNOW, 56(4), 30–33, 2014
[18] J. Pollet, “Innovative Defense Strategies for Securing SCADA & Control Systems”, Technical Papers of ISA, 459, 115–128, 2005
[19] R.A. Rodríguez-Gómez, G. Maciá-Fernández, P. García-Teodoro, “Survey and taxonomy of botnet research through life-cycle”, ACM Computing Surveys (CSUR), 45(4), 2013
[20] A. Sanatinia, G. Noubir, “OnionBots: Subverting Privacy Infrastructure for Cyber Attacks”, arXiv preprint arXiv:1501.03378, 2014
[21] M. Sikorski, A. Honig, “Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software”, No Starch Press, 2012.
[22] S. Soltani, S.A.H. Seno, M. Nezhadkamali, R. Budiarto, “A survey on real world botnets and detection mechanisms”, International Journal of Information and Network Security (IJINS), 3(2), 116-127, 2014
[23] K. Stouffer, J. Falco, K. Scarfone, “Guide to industrial control systems (ICS) security”, NIST special publication, 800(82), 16-16, 2011
[24] ThreatSTOP, Black Energy, Security Report by ThreatSTOP, 2016
[25] A. Vasudevan, R. Yerraballi, “Spike: engineering malware analysis tools using unobtrusive binary-instrumentation”, In Proceedings of the 29th Australasian Computer Science Conference, Australian Computer Society, Inc., 2006, 48, 311-320.
[26] G. Vigna, “Malevolution: The Evolution of Evasive Malware”, Keynote on the 10th Conference on Detection of Intrusions and Malware & Vulnerability Assessment (DIMVA), 2013